Welcome, I don't have much going on here yet. Maybe check out my latest blog post?
sunshinectf 2022 writeups part 1
2022-11-21
This past weekend, I participated in SunshineCTF along with ProjectSEKAI. We were able to get full solves on all of the challenges across the board and place 1st!
Below are some of the challenges that I helped to solve.
MiddleEndian (rev, 150pts, 47 solves)
Here at Chompy Game Studios, we have developed a brand-new byte ordering scheme: middle endian! This transformative scheme will surely impress our shareholders! Can you reveal the secret contained within?
We're given a file called flag.png.me. My initial impressions were that we just needed to re-order the bytes of the file to reconstruct the PNG.
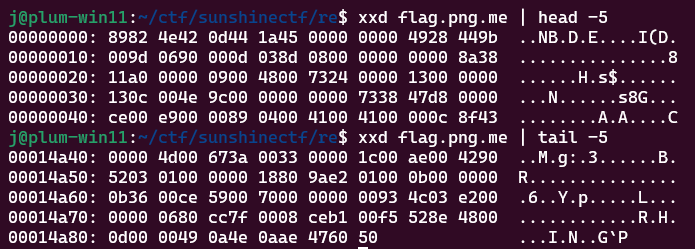
Knowing that the PNG files are identified with the magic bytes 89 50 4E 47 0D 0A 1A 0A, we can see that the first byte is at the beginning of the file, the second byte at the end of the file, the third byte at the beginning, fourth byte at the end, etc.
We can write a short script that splits the file into two streams of bytes, based on an odd or even index, reverse the latter stream, then weave the two streams back together.

Exotic Bytes (crypto, 50pts, 127 solves)
Our researchers at CoolCryptoGames have been designing a new encoding algorithm for our Korean customers that is just as efficient as plain ol' text. However, they kind-of forgot how to decode their own algorithm, so can you help them decrypt this so they can patent it?
We're given a string of gibberish Korean text that presumably decodes to a flag: 걳걵걮걻걢갴걳갳걟갱갲갸걟갱갵걟걢갱건걟걲갳걭갴거거갱걮걧걽.
Tossing it into CyberChef's Text Encoding Brute Force block and examining the different outputs yields us the flag: sun{b4s3_128_15_b1t_r3m4pp1ng}
Listy (web, 150pts, 17 solves)
I made a little leaderboard listy app, it's a bit rough so please don't judge me too harshly.
We're given a link to a web app without much going on.
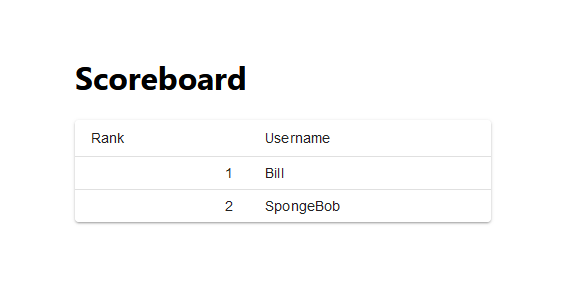
Inspecting robots.txt yields:
Disallow: *
Disallow: /dev #TODO: Separate off dev branch (https://todo.sr.ht/~listydev/Listy/5)
What we stumble upon is presumably the source code used for this webapp, and a ticket signaling that the dev environment ought to be split from prod.
We can inspect the source tree to check out some of the source files, and notice that it's a NextJS application that calls to a Google Cloudfunction as its backend.
The README.md says that we can run invoke.sh to invoke the cloud function:
#!/bin/bash
# Ansible-Vault unlock the gcloud credential
CRED=$(ansible-vault decrypt vault.txt --output /tmp/key.json)
gcloud auth activate-service-account listy-developer@sunshine-2022-challenges.iam.gserviceaccount.com '--key-file=/tmp/key.json'
rm /tmp/key.json
curl -H "Authorization: bearer $(gcloud auth print-identity-token)" https://us-central1-sunshine-2022-challenges.cloudfunctions.net/listy\?bucket\=ssctf22-listy-leaderboard-prod
Ok, so the application has an encrypted credential that is needed in order to authenticate and call the cloud function. Trying to decrypt the vault with no password doesn't seem to work. How can we find the password?
Digging through the other tickets raised on the repo, we found ticket #4:
Currently, I'm just using a local script w/ a vaulted file for storing a service account. Maybe pull from the gcloud command natively? For now I'm just vaulting with my email to keep secrets scanners from bugging me.
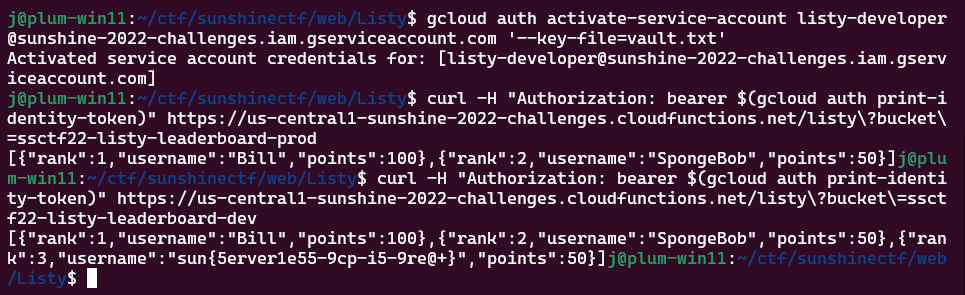
We decided to try the author's email as the password for the vault. The Google Cloud service account email that we found in the source tree didn't work as the password, but a teammate found a different email in the git logs: dev@listy.com
Doing so decrypted the vault, giving us JSON credentials and now allowing us to run the cloud function.
Changing the bucket argument in the cloud function from prod to dev gives us the flag:
I'll have a few more challenges written up in a separate post.